Aranya is an access governance and secure data exchange platform for organizations to control their critical data and services.
© 2025. All rights reserved.
A product specification of the standalone Aranya daemon. The goal is to provide a commercial off the shelf solution for integrating Aranya. Customers should be able to download the Aranya daemon, setup a team, and begin using Aranya.
Primary Goals:
Secondary internal goals:
Aranya is a decentralized message delivery platform with authorization built in. Below are some basic requirements for running the beta version of Aranya:
System Requirements:
After the beta is working, the following values should be measured to estimate system requirements:
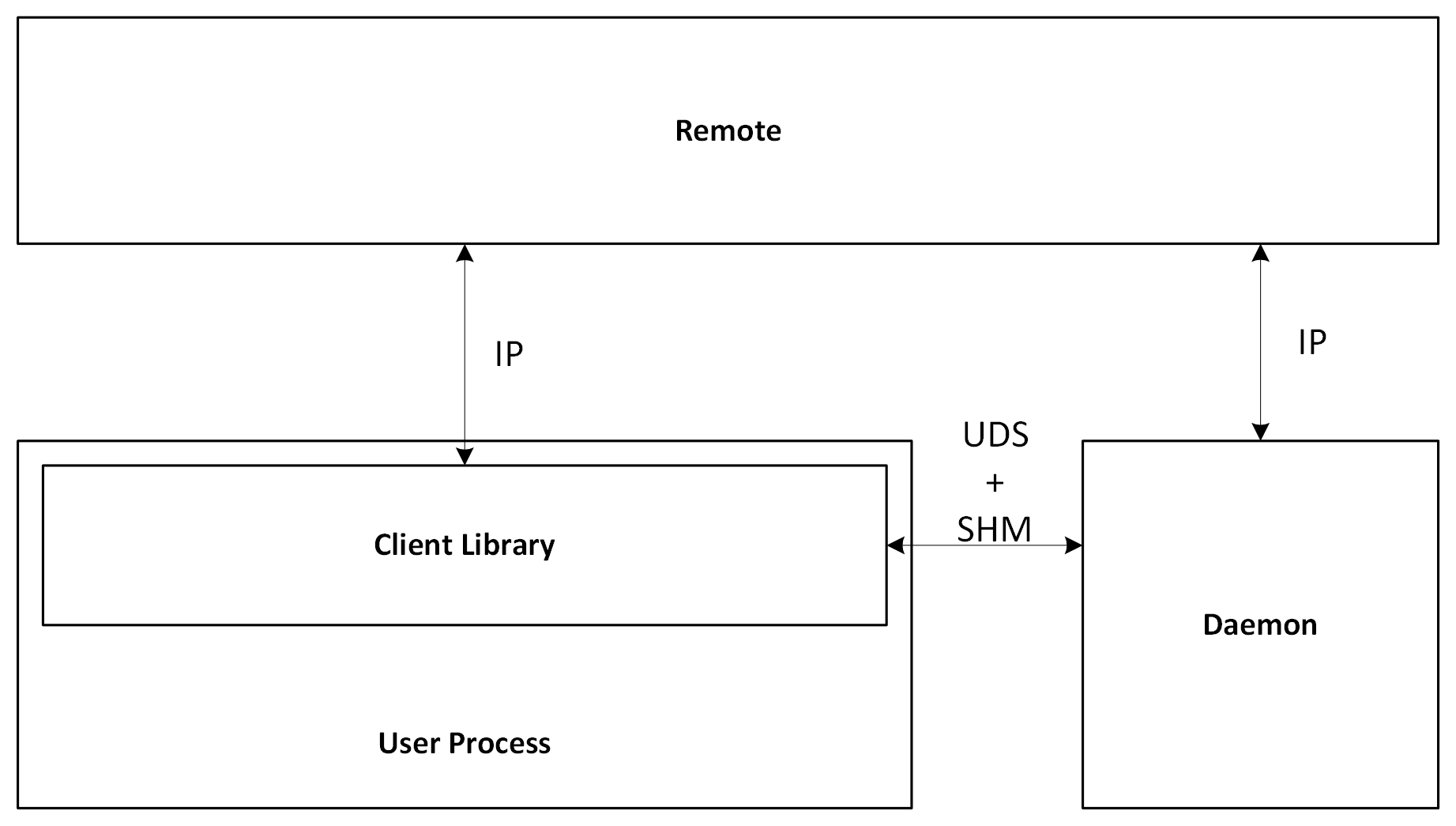
There will be two subsystems as part of Aranya:
The daemon is a standalone process that runs Aranya and exposes the control plane API via IPC. The daemon will periodically sync with peers and handle commands as they are synced. The current design does not require any disk-persisted effects, so on startup the daemon should start from a clean state (aside from loading accounts) every time it is started. This includes clearing any shared memory on startup to avoid collisions/stale data.
The client library exists inside the user’s process and is used to interact with the daemon. The client library also includes a light wrapper around AFC allowing the user to encrypt data and send messages to peers.
Both subsystems are limited to a single KeyBundle per process to limit the possibility of leaking device keys. This still enables the daemon to participate in multiple teams by using the same keybundle for every team.
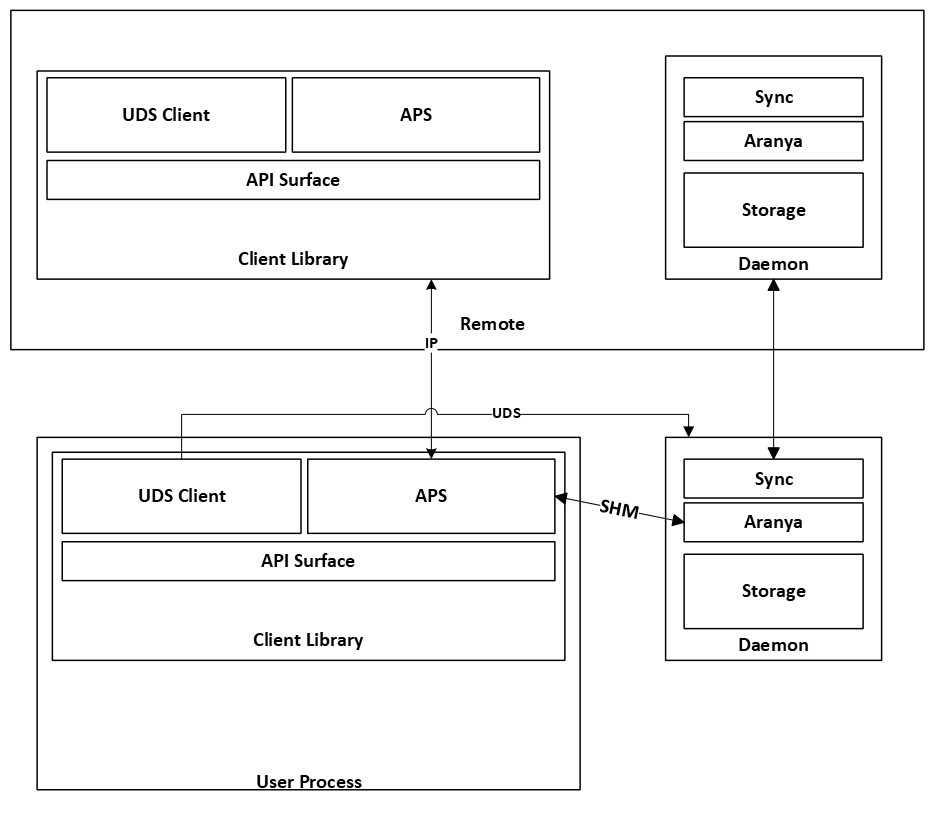
For V1, we will initially design for the C API. The Rust client library is a bonus that we gain from the Rust -> C compilation. The C API should include autogenerated docs.
Config
On startup, the daemon requires the work directory as well as the path to the UDS socket that should be created. All other config values are provided when a client context is initialized and passed to the daemon over the UDS socket. This approach allows the user API to drive the configuration of the daemon, and can help reduce errors in config mismatch by minimizing the number of duplicate config values.
The system is made up of multiple components:
The “client API” is the top level component and contains local operations such as enabling/disabling syncing or initializing a new device.
The Access Control Plane is the top level control plane, enabling IDAM operations and other on-graph operations. The Access Control Plane is used to manage keys, address assignment, roles, and labels as set out in the policy.
For the beta, the AFC Plane will be build to provide a simple API for sending and receiving messages using AFC. The AFC Plane contains its own control plane for control messages, as well as the main data plane for moving data between devices.
Component structure:
The client APIs are local only API endpoints that do not create commands on the graph. They are mostly used to manage the local state.
No policy command associated with these commands.
Beta:
Easy to implement, key moving is done by integration.
MVP:
We will provide an additional optional onboarding API:
TODO: we need a flow chart or just event sequence for these.
The goal of this onboarding API is to simplify the process of onboarding a user/device by providing an invite code instead of passing a KeyBundle.
The IDAM control plane is for managing identity and authorization by interacting with the graph. Each endpoint creates one or more commands on the graph.
The IDAM control plane will be managed by the daemon process which will be accessed with the previous APIs via an IPC mechanism. The daemon will be responsible for syncing state with peers. To enable, these two additional APIs will be provided to add and remove peers to sync from:
Initially, UDS and shm will be used for IPC between the daemon and client library.
Role APIs need improvement post beta (to support custom roles?).
The AFC plane is split in two different sub-planes: the AFC control plane and the AFC data plane. The AFC control plane is responsible for any Aranya command or ephemeral commands, while the AFC data plane contains only data related APIs.
ReadData.For the initial implementation in the beta, AFC control messages should be handled transparently by the client library. In the future, control messages can be passed to the user to be manually forwarded to the daemon using a different API.
There will be 4 different user roles with the following set of permissions for each.
owner
owneradmin
operatoroperator
user
sync-role
Notes:
API documentation must be provided for the client API covering the functions and behavior of each API call. Most likely, this will take the form of a doxygen-like web page. Developers can use this to look up language agnostic functions for operating the client API. The documentation should also include tutorials and a quickstart to get developers up and running with Aranya as soon as possible. Documentation should also be provided for the daemon so that developers and sysadmins can understand the requirements and operations of the daemon.
AFC - the library used to do high performance encryption using keys managed by Aranya.Aranya - the main library that drives the control plane and policy execution.daemon - a long-lived process, typically running in the background, that
handles commands and keeps state.device - a computer, sometimes associated with a user but can also be independent.
In this model, we consider devices instead of users directly to accommodate
autonomous entities.IPC - inter-process communication.policy - an Aranya policy, containing the logic and rules of the system.sync - a request to synchronize the commands on the control plane. Syncs are currently
pull only, so the device that requests a sync receives commands from the requestee.team - a group of devices with an associated policy.UDS - Unix Domain Sockets, used for communication between processes.user - a person who may operate a device.Future Client APIs might include endpoints for Fact DB queries.